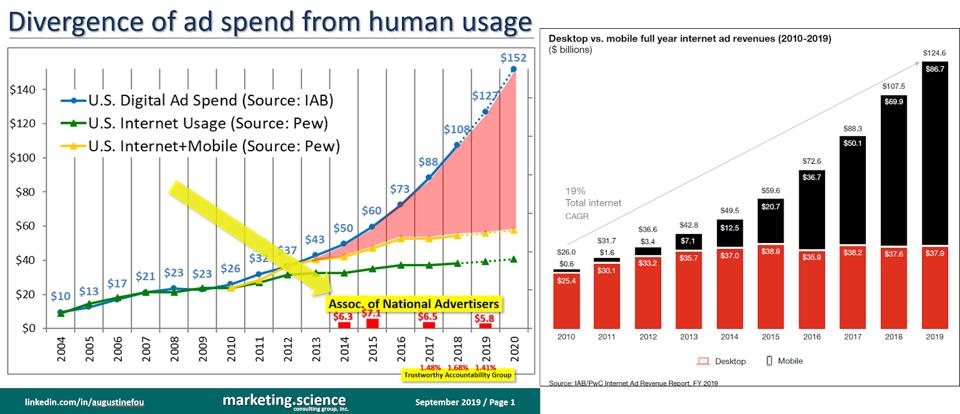
As more and more billions of dollars poured into digital advertising, and specifically into mobile, bad guys found it easier and easier to make more and more money. Practically all of the additional digital ad spend from 2012 onward went into mobile (black) while desktop (red) remained flat since then (right). There also appears to be a striking resemblance to the “red area” that opened up dramatically since 2010. That red area represents the difference between digital ad spend (blue line) and Internet and Mobile usage by real humans (green and yellow lines); according to Pew Internet those two lines flattened out since 2013, suggesting a “maxing out” of actual humans using the internet and mobile devices. But digital ad spend continued to shoot upward. Hmmm...
On the surface, advertisers thought they were showing more ads to more humans, who were using mobile more. But below the surface, fraudsters were happily making off with more and more ad revenue. Mobile fraud is so easy to scale; there are so many forms of it; and all of these mobile tactics are LESS measurable for fraud, by IVT (invalid traffic) detection technologies.
Augustine Fou (left), IAB (right)
Mobile Geolocation Fraud
Advertisers assumed that because humans were using mobile devices, they could target ads to them based on their geolocations. So they paid more for the extra targeting. Fraudsters quickly figured out that if they just added lat-long parameters into bid requests, they could earn more money. Those locations didn’t have to be accurate; and they didn’t even need to be real. Advertisers never asked anyway; they just paid more for bid requests that contained location information.
Further Reading: Solving Location Fraud With Proper Arrival Attribution
CPM Fraud - More Mobile Display Ads
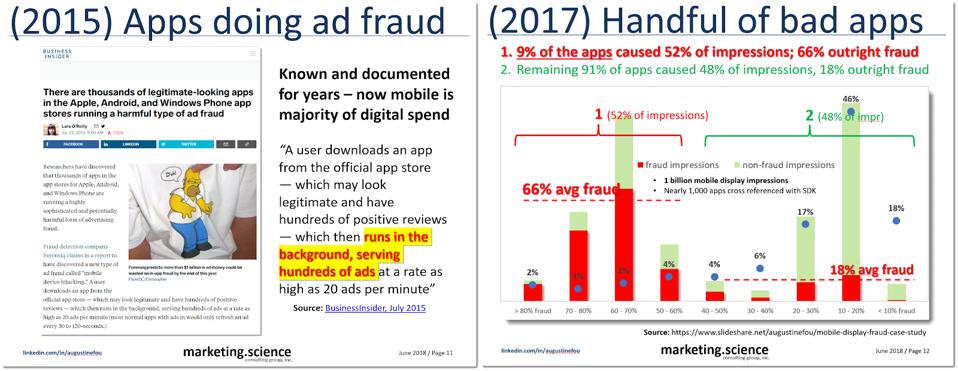
For those ads sold by the thousands (CPM - cost per thousand), bad guys could make more money by showing more ads. Since programmatic buying and selling took off in 2013, there have been case after case of mobile apps documented to be committing ad fraud - for example, flashlight, keyboard, selfie camera, and alarm clock apps loading ten of thousands of ads in the background, continuously throughout the day, whether the app was in use or not, and whether the mobile device was in use or not. Advertisers just wanted more quantities of ads to buy, and these mobile apps happily obliged.
Augustine Fou / Marketing Science
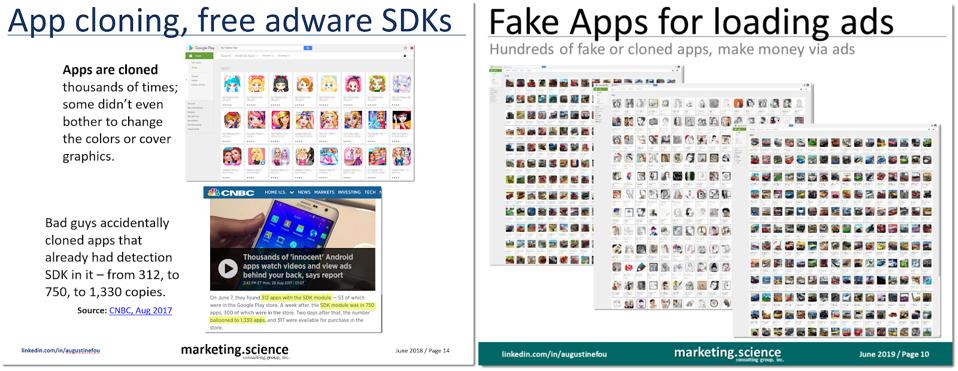
How do bad guys scale the fraud even more? Right, by handing out free SDKs (software development kits) that other mobile app developers could simply build into their apps to start running ads, sharing some of that sweet, sweet ad revenue back to the SDK developer, of course. With someone else’s SDK in your app, all sorts of shenanigans can be had, too. Aside from making it easy for more developers to make apps and run ads, why not clone the apps themselves. Some fraudsters took the same app and cloned it hundreds, or thousands of times. And only some of them made the extra effort to even change the app icon. Most of them didn’t bother. On top of cloning apps, fraudsters also cloned their developer accounts. That way, even if Google Play Store banned a developer, they would have dozens of other cloned developer accounts to continue making money with dozens of apps each.
Augustine Fou
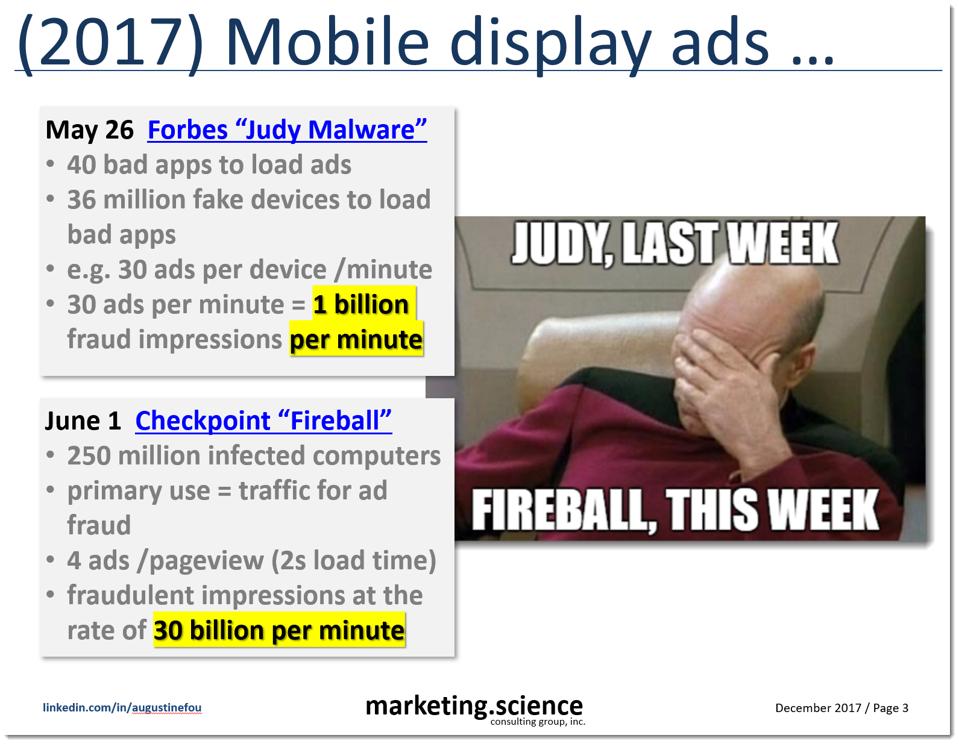
Apps with billions of downloads were documented committing ad fraud and harvesting consumers’ private information at scale [1], [2], [3], [4]. But if waiting on unsuspecting humans to download and install apps is too slow and tedious, fraudsters can spin up millions of mobile emulators in data centers. These pieces of software are used by developers to test their apps before launch. But the same software can be used by fraudsters to download, install, and use mobile apps continuously for the purpose of generating ad impressions - for example a fake mobile device can play hyper casual mobile games continuously 24/7 while humans could not. By combining mobile apps designed solely to load ads, with fake mobile devices designed solely to keep those apps running continuously, fraudsters could multiply the fraudulent ad impressions to the tune of 1 - 30 billion ads per minute. Even if only a fraction made it past fraud detection, it was highly profitable due to its sheer scale.
Augustine Fou
CPC and CPI Fraud - More Clicks and Installs
Marketers were also paying for clicks and installs, thinking that optimizing their campaigns with these metrics meant they were optimizing for “performance.” Fraudsters usually do the exact thing that marketers are willing to pay for. If marketers paid by clicks (CPC - cost per click), fraudsters would generate clicks using their mobile apps. This is trivial. If marketers paid by install (CPI - cost per install), fraudsters would use their mobile emulators to download and install the apps. Of course fraud detection would try to catch them by looking at post-install behaviors. If the app were never used after install, if it were opened too soon after install, etc. it could be marked as invalid. But fraudsters could easily fake anything that was needed to get by fraud detection, including opening the app once a day for five days straight, to make it count as a “valid” install and thus get paid the CPI bounty.
Further, fraudsters use malicious mobile apps to generate a flood of fake clicks to trick attribution systems into thinking installs happened (when they didn’t) and pay out the CPIs. The fraudulent clicks can also be timed to coincide to users’ clicks on ads, the initiation of the download of an app, or even other post install events - this is because malicious SDKs can listen to other events on the device. These clicks are designed to take credit for app installs, even the organic installs that would have happened anyway — a form of fraud known as “organic stealing.”
Further Reading: Uber is Suing 100 Mobile Exchanges for Ad Fraud
Android vs iOS
Depending on the operating system - Android vs iOS - there are some limitations to what forms of fraud can be accomplished, but there are also additional things fraudsters could do beyond running more ads, or faking clicks and installs. It is widely known that there are far more fake or malicious Android apps than iOS apps. Apple is far stricter in their app approval process and that’s the main channel for getting apps on real humans’ iOS devices. On the other hand, it is trivial to get Android apps approved by Google Play; if Google Play doesn’t approve an app there are many alternatives for distribution, including “third party” app stores.
The differences in the operating systems themselves allow for different, additional exploits. For example on Android, one app can ask for permissions to install or uninstall other apps, listen for the installation or uninstallation of other apps, turn on and of the microphone and camera, turn on and off network connections, keep the device from sleeping, etc. Some or all of these can be used in combination to commit more ad fraud or steal more user data. iOS is far more locked-down as an operating system.
Mobile Fraud is a Many-Splendored Thing - for the Fraudsters
And, by the way, did I mention mobile ad fraud is harder to measure? That’s because the fraud detection companies’ javascript tags don’t work well, or don’t work at all, in mobile app environments. So the more money that pours into mobile advertising, the more easily fraudsters get away with the fraud, all while advertisers get fraud detection reports that appear to show there is low to no fraud in mobile. I’ve literally heard marketers say, “there’s so little fraud in mobile, let’s shift all our ad budget to mobile!” If that isn’t music to fraudsters’ ears, I don’t know what is.
"Mobile" - Google News
August 24, 2020 at 03:48PM
https://ift.tt/3aVKYoU
Mobile Ads Are SO Lucrative (For The Bad Guys), Even CFOs Would Be Jealous - Forbes
"Mobile" - Google News
https://ift.tt/2P9t7Cg
Shoes Man Tutorial
Pos News Update
Meme Update
Korean Entertainment News
Japan News Update
Bagikan Berita Ini














0 Response to "Mobile Ads Are SO Lucrative (For The Bad Guys), Even CFOs Would Be Jealous - Forbes"
Post a Comment